Cyber Security - a how to guide
Working remotely means you need to find a balance between supporting your staff and volunteers to access your systems, and securing them against cyber attack.
External cyber attacks are becoming increasingly indiscriminate. Assuming you will not be a target is no longer an option. Charities have already been targeted. The cost of failure is huge and can mean reputational damage which is impossible to recover from.
Cyber security expert Derek Gordon has been working on high profile global security projects with PwC for over twenty years. He emphasised the key areas charities need to think about on our DigiShift webinar on Cyber Security for Third Sector Organisations.
Derek highlighted cyber security is really not just an IT issue.
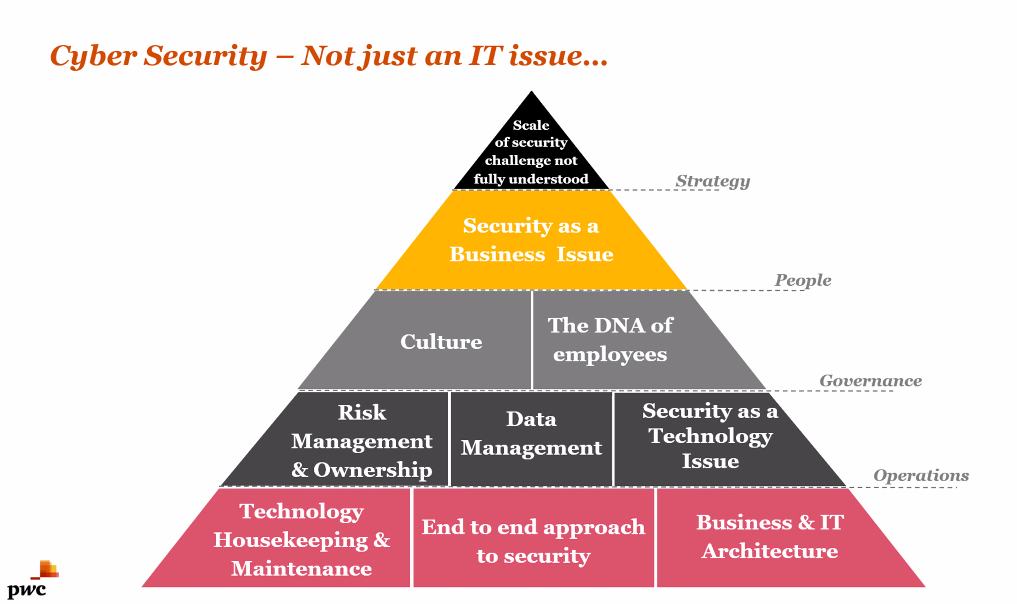
Your own people are your biggest risk
Your staff and volunteers are the biggest weakness in your cyber security defences.
“81% of hacking-related breaches leveraged either stolen and/or weak passwords”
Verizon Data Breach Survey 2017
So it is essential you and your people have good cyber awareness. Derek shared this fun 2 minute video to show how insecure many people’s passwords are and how easily people disclose passwords to strangers.
Phishing continues to be a successful strategy for attackers
Phishing is the fraudulent practice of sending emails purporting to be from a reputable source. Their purpose is to induce people to reveal personal information or provide financial details.
Attackers rely on poor staff awareness and poor password management, combined with gaps in an organisation’s patching.
An example of a recent phishing attack on SCVO saw emails to staff, which looked to come from our chief exec. The email asked staff for a quick favour in an emergency. Anyone replying was asked to by gift cards and provide details by return email.
Phishing can also be used to deliver malicious software. This is commonly called malware. A specific type of malware, called ransomware, tells the user they must pay a ransom to fix their computer. You should never pay a ransom.
There is a good guide to protection against phishing in the NCSC (National Cyber Security Centre) Small charity guide.
Educating staff on cyber security should be a key strategic priority!
Your staff need to be aware of the cyber risks to your organisation and their role in protecting you. We like NCSC’s quick 30 min cyber security e-learning course for staff, introducing why cyber security is important and how attacks happen.
Do you have a positive security culture?
This is about encouraging curiosity and not pressuring staff to work so fast that they don’t have time to consider risk. It can also be as simple as regularly repeating security messages and staff training.
Your staff may feel embarrassed to report that they have "fallen" for a scam or attack. So you need to be open and clear that staff should always report any issues without repercussion.
What you should do right now to protect your organisation
Derek highlighted repeatedly that if you can make yourself less vulnerable than someone else, then the hacker will likely move on to the easier target.
The first things to think about are the 3 P’s - patching, passwords and privilege.
Patching
Patches are software updates, often to fix bugs or security vulnerabilities. You should ensure all software is up-to-date; and that antivirus and malware scans are run regularly.
Passwords
Passwords should be strong and unique. Passwords should be changed regularly and not written down anywhere. Encourage your staff to use a password manager. A further layer of security can be added by using 2-factor, or multi factor, authentication.
Privilege
Privilege is about the levels of access different users have to different parts of your system. This should be checked and updated regularly. Who has admin rights to your systems? Do they need to have this? Do you routinely update access rights when people change job roles, or leave your organisation?
What you should do next
Derek advises organisations move beyond good security practice and start to consider strategy.
This is mostly about good governance to change the way you think, work and behave. Derek’s colleague Dr Richard Horne provides helpful measures to consider in his paper Know the game, not just the rules.
Management and boards should work to understand your current cyber security maturity and identify vulnerabilities. NCSC Cyber Essentials self-assessment scheme helps you to guard against the most common cyber threats and their certification demonstrates your commitment to cyber security. Scottish Government’s Cyber Resilience Unit is currently producing a weekly Cyber Resilience Bulletin sharing important cyber security information from trusted sources. Derek recommends the NIST framework to help you improve your cybersecurity risk management.
You should develop a plan:
- How you would approach a major security incident?
- Can your organisation rapidly respond to incidents, threats and security events?
- Do you have secure backups & feel confident you can restore your systems?
- Are you prepared?
Organisations who have tried and tested response processes are those least impacted by an incident. Our Cyber Resilience Co-ordinator Alison Stone recommends you plan for the worst and hope for the best. NCSC Exercise in a Box can help you do exactly that! This is an online tool to help you find out how resilient you are to cyber attacks and practice your response in a safe environment
You must also check you have appropriate processes in place for securing your data. You will need to understand how you manage data; and how you share data with other organisations and your software suppliers. Is it protected? Which partners do you share your critical information with and are you confident that those partners are protecting it?
Finally, it comes back to your people. Are you sure your people are using your processes correctly and understand why you have put them in place?
I had a lightbulb moment during these cyber talks. Cyber security is a lot like fire safety planning. You need strategies to protect your assets! So you
- identify the risks and put strategies in place to minimise them
- you educate your staff about the risks and your policies
- you regularly practice and improve your emergency plans so your staff are prepared and protected
- your goal is to not have to call in the emergency services
Do you have a fire safety policy? Do you have a cyber security policy? What about a cyber security strategy?



